November 14, 2016 Alex Woodie
IBM i customers should stop using 3DES, also known as Triple DES, ciphers due to the SWEET32 vulnerabilities that could leave sensitive information unprotected as it moves between client and server via the OpenSSL and OpenVPN protocols. This was the gist of a security alert sent last week by IBM, which also issued new PTFs to address the problems in its own IBM i products. On November 4, IBM issued security bulletin N1021697, which discussed what to do about so-called SWEET32 security vulnerabilities in OpenSSL and OpenVPN. The security problems, which are detailed in CVE-2016-2183 (for OpenSSL) and CVE-2016-6329 (for OpenVPN), impact all releases of the IBM i OS, from 6.1 to 7.3. IBM issued a batch of new PTFs to address the security vulnerabilities, both of which were given a low severity rating of 3.7 on the 10-point CVSS score, largely due to high level of complexity that a successful attack would entail. Per IBM's security alert (which you should definitely read to understand mitigations and workarounds), the PTF numbers that should be applied are as followed:
If you read our October 3 story about the last batch of OpenSSL patches, you will recall that IBM already issued the SI62622 and SI62623 patches. So what's with the new round of patches? Two things. First, IBM is now patching the SWEET32 flaws in OpenVPN, and it's also covering IBM i 6.1 and 6.1.1 with the patches; only IBM i versions 7.1 to 7.3 were patched in October. The PTFs essentially disable 3DES across all IBM-controlled programs and utilities, including the SSL/TLS facilities in the IBM i Licensed Internal Code (LIC); the OpenSSL implementation in PASE; the Java JSSE-based IBMJSSE2 utility; and Domino, which contains an embedded SSL implementation (although it also uses the System SSL/TLS facility in some configurations). The PTFs will activate newer and more secure AES ciphers in these IBM products. 'Not disabling the Triple DES (3DES) cipher or algorithm will expose yourself to the attack described above,' IBM writes in its security alert. Why is 3DES being removed? Simply put, it's because 3DES is not considered highly secure anymore. The reasons have largely to do with the fact that the 3DES algorithm uses 64-bit block sizes, and those block sizes are no longer deemed sufficient by the security community to keep vigilant cybercriminals at bay. AES, by comparison, uses a 128-bit block size, which makes a big difference in preventing potentially sensitive data that could expose plaintext keys from leaking out. 'It is well-known in the cryptographic community that a short block size makes a block cipher vulnerable to birthday attacks, even if there are no cryptographic attacks against the block cipher itself,' write security researchers Karthikeyan Bhargavan and Gaëtan Leurent on the website sweet32.info, which is an excellent source for information on the SWEET32 vulnerability and how hackers can pull off brute-force 'birthday' style attacks that uses the laws of probability and big data to crack one-way hashing algorithms. With the 3DES algorithm encrypting data across an HTTPS connection, the researchers determined that an attacker executing a SWEET32-based birthday attack could retrieve the plaintext keys (in the form of HTTP cookies) by capturing about 785GB of traffic between a Web browser and a server. That would require the HTTPS connection to be live for about two days, which may sound impractical (and is why the vuln garnered a relatively low security threat rating). But considering the financial motivation that hackers have and the increasingly sophisticated tools at their disposal, there's no reason to take a chance by using older, weaker cipher technology when newer and stronger ciphers like AES are readily available. The good news is that 128-bit AES encryption is still considered practically unbreakable and is supported in popular network security protocols like OpenSSL, TLS, and SSH. AES (which is also available in 256-bit strength) should be considered the only safe encryption algorithm to use at this point. Many popular websites use it, and Web browsers support it. It's supported in the IBM i stack. The bad news is that there's still a lot of 3DES out there. Because some Web browsers enable 3DES before AES by default, and because there are a lot of misconfigured servers out there, AES is still used in 1 to 2 percent of the world's Web traffic secured with the TLS protocol, according to Bhargavan and Leurent. (SSL, you will remember, is considered weak; TLS is its replacement.) For IBM i shops that take security seriously, it's important to get on the right side of this. IBM is eliminating 3DES from its products. But the average IBM i shop runs a lot of non-IBM code, including FTP and Telnet utilities developed by third-party vendors. This is why it's critical for IBM i shops to check their software inventory and upgrade all of the vulnerable products. According to IBM i security expert Patrick Townsend, this should be a priority item for IBM i shops. 'This one is important and you should take a look at it right away,' he writes on his Data Privacy Blog. While Townsend Security uses the IBM i System SSL/TLS library in its products and is thus protected via IBM's remediation work, there are a handful of third-party software vendors that have their own implementations of OpenSSL, which requires them to fix the problem themselves. Customers will need to make sure that 3DES is being removed from these special ports of OpenSSL, he says. 'You need to be talking to them right away,' Townsend writes in the blog post. 'Unfortunately I know of one or two that are no longer supporting the IBM i platform. So you may have some difficulty getting resolution on this issue.' You can read IBM's security alert at www-01.ibm.com/support/docview.wss?uid=nas8N1021697. RELATED STORIES |
3DES is probably the most studied cryptographic algorithm ever. It offers the strength equivalent to a 112-bit block cipher. The best attacks published require massive amounts of storage and still take more than 2 108 operations. CAST is a well studied 128-bit algorithm. There is no known way of breaking it faster then brute force. The average rectum is roughly 12 centimeters (about 5 inches) long, but you're better off listening to your body than focusing on that number. Take fisting, for example. Triple DES encryption process It works by taking three 56-bit keys (K1, K2 and K3), and encrypting first with K1, decrypting next with K2 and encrypting a last time with K3. 3DES has two-key and three-key versions. Using the fastest computer in the world you will be able to process 2.932848e+24 possible combinations per year. 930.10^15. 60. 60. 24. 365 = 2.932848e+24 If you had this super computer running all day every day to crack one single encryption key of 128 bits. I would take roughly 68.5 years to go through all the possible combinations. Add just one more character ('abcdefgh') and that time increases to five hours. Nine-character passwords take five days to break, 10-character words take four months, and 11-character passwords take 10 years. Make it up to 12 characters, and you're looking at 200 years' worth of security – not bad for one little letter.
Think your password is secure enough?
How Long Does It Take To Crack 3des For Pc
You may want to think again. In 2014, nearly half of Americans had their personal info exposed by hackers – and that doesn't even count the many companies that experienced breaches.
And with more and more businesses storing their information in the cloud and using SaaS solutions like business intelligence and hr software platforms, keeping your information safe becomes even more important.
Selecting an obscure and complex password and changing it frequently can spell the difference between keeping your data secure and having your personal information stolen. We've gathered insights and advice to empower you to tighten up your online security – and keep hackers out of your personal business.
To get started, we set out to discover just how quickly a seasoned cracker could 'brute-force' various types of passwords (systematically check combinations until finding the correct one) based on factors such as length and character types. We also created an interactive feature that lets you estimate how long it would take someone to crack a password now compared with how long it took in the past. If you come up with an idea for a potential password, our tester can tell you just how secure it is. Just how many days, weeks, or years worth of security an extra letter or symbol make? How does password strength change over time? The answers just might surprise you.
How strong is a typical password now – and how strong was it in the 1980s? Enter a word (not your current password) and drag the slider to select a year to find out how long it would take for someone to crack the term if it were your password. It could take anywhere from infinite time to a millennium to mere fractions of a millisecond.
You can turn the 'word list' function on or off as you test passwords. This tool works by cycling through a word list containing common words and passwords and then evaluating other factors such as character types. If you enter a password not on the word list, the cracking time will not be affected. But if your password is on the word list, it greatly affects cracking time.
Note: The interactive tool is for educational purposes only. Although it does not collect or store your passwords, you should avoid using your current password.
How long should your password be?
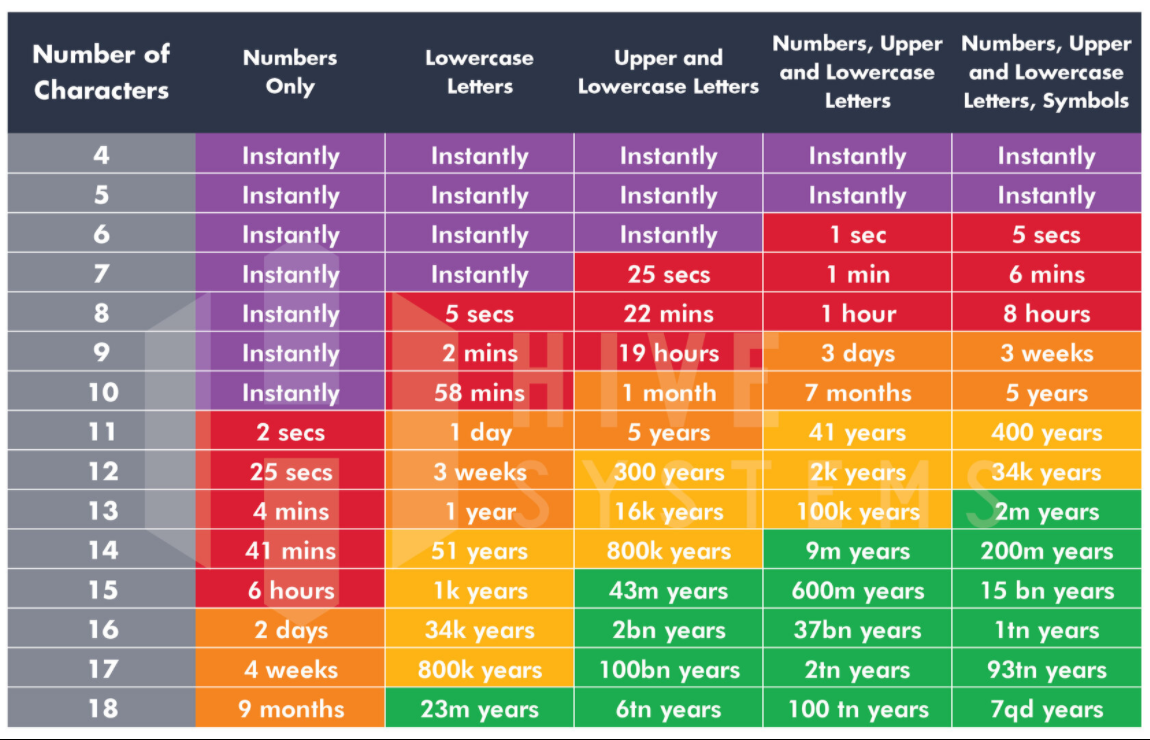
When it comes to passwords, one thing is certain: Size matters. Adding a single character to a password boosts its security exponentially. In a so-called 'dictionary attack,' a password cracker will utilize a word list of common passwords to discern the right one. The list above shows the difference that adding characters can make when it comes to security.
For instance, if you have an extremely simple and common password that's seven characters long ('abcdefg'), a pro could crack it in a fraction of a millisecond. Add just one more character ('abcdefgh') and that time increases to five hours. Nine-character passwords take five days to break, 10-character words take four months, and 11-character passwords take 10 years. Make it up to 12 characters, and you're looking at 200 years' worth of security – not bad for one little letter.
alpha and numberic characters
Combining numbers and letters rather than sticking with one type of character dramatically enhances password security. A string of nine letters or numbers takes milliseconds to crack. Add a single letter, and your password may become cryptic enough to thwart password crackers for nearly four decades.
However, it's not as simple as swapping your 'e' for a '3' or adding a number at the end of a string of letters. Password attacking methods actually take advantage of those common habits. Your best bet is to simply make your password less predictable and more complicated.
asci, lowercase, and numeric characters
Combining several types of characters is an extremely effective way to make your password more cryptic. A simple, common word can be cracked in fractions of a millisecond. Inject a mix of lowercase and uppercase letters, numbers, and symbols (think @, %, and #), and your password can be secure for more than a decade.
password strength over time

Not every security issue comes down to password character types and length – time is also a major factor. Over the years, passwords weaken dramatically as technologies evolve and hackers become increasingly proficient. Castlevania the dracula x chronicles usa psp iso cso download. For example, a password that would take over three years to crack in 2000 takes just over a year to crack by 2004. Five years later, in 2009, the cracking time drops to four months. By 2016, the same password could be decoded in just over two months. This demonstrates the importance of changing passwords frequently.
How Long Does It Take To Crack 3des For Windows 10
what if you get hacked?
One morning, you open your email, and everything has gone haywire: Friends are chatting you to say they've received spam from your address. Your login history looks odd. You have a pile of bounce-back messages in your inbox and a bunch of strange messages in your sent box. You've been hacked – so what should you do?
First, recover your email account, and change your password (use our guidelines to formulate a strong one). Complete all the steps, such as changing security questions and setting up phone notifications. Because email is filled with personal information, you should also notify your bank, PayPal, online stores, and any other accounts to discern whether a breach has occurred. Be sure to change other passwords as well. Finally, notify your contacts in case emails sent from your account have compromised their information too. While not getting hacked at all is the best-case scenario, promptly taking these steps can make the best of a bad situation.
Protect yourself
As time goes on, it only becomes more likely that your password will be hacked – putting your most personal information at risk. By taking a few steps to enhance your password, you can exponentially minimize the risk of a breach. When it comes to passwords, size trumps all else – so choose one that's at least 16 characters. And be sure to choose a mix of character types (numbers, uppercase and lowercase letters, and symbols) to further enhance its security.
What else can you do? Steer clear of words found in the dictionary, pronouns, usernames, and other predefined terms, as well as commonly used passwords – the top two in 2015 were '123456' and 'password' (yes, you read that right). Also, never use the same password in different places (that forgotten account at a site you never use could lead to a bank account breach). Consider using a password generator in order to get a complex password with no discernible pattern to help thwart password crackers. Finally, if memorizing long strings of characters proves too taxing, consider adopting a password manager that stores all your passwords. No password is perfect, but taking these steps can go a long way toward security and peace of mind.
Methodology
Using processor data collected from Intel and John the Ripper benchmarks, we calculated keys per second (number of password keys attempted per second in a brute-force attack) of typical personal computers from 1982 to today.
The results from our interactive feature may differ from those of other online password-testing tools due to factors such as different equations, processors, and word lists.
Our data are based on the following equations:
Number of possible character combinations:
(Password Type)^(Password Length)
Password Type is the number of possible characters.
Effective Cores:
1/((1-Efficiency Constant)+(Efficiency Constant/Processor Cores)) The Efficiency Constant we used is 0.99, and we assume that 99% of the processor's operations can be dedicated to the password crack.
Processor GFLOPS:

How Long Does It Take To Crack 3des For Windows 7
Processor Frequency * Effective Cores
Keys Per Second:
How Long Does It Take To Crack 3des Free
GFLOPS/Encryption Constant (gathered and calculated from John the Ripper benchmarks).
Time in seconds:
Seconds = Combinations/KeysPerSecond
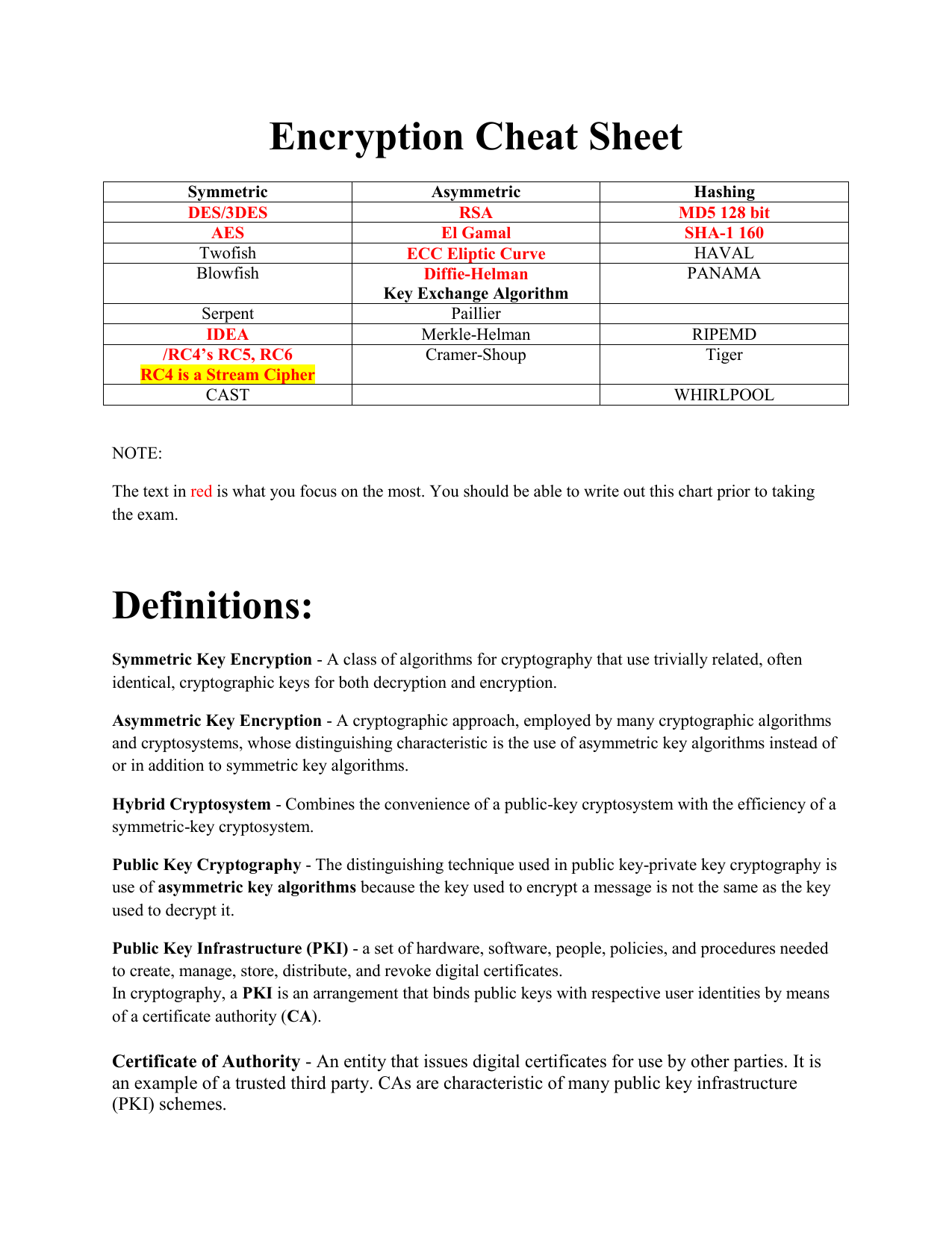
- Release 6.1 – MF62786, SI62465
- Release 6.1.1 – MF62785
- Release 7.1 – MF62779, SI62463, SI62623
- Release 7.2 – MF62778, SI62464, SI62622
- Release 7.3 – MF62780, SI62586, SI62622
If you read our October 3 story about the last batch of OpenSSL patches, you will recall that IBM already issued the SI62622 and SI62623 patches. So what's with the new round of patches? Two things. First, IBM is now patching the SWEET32 flaws in OpenVPN, and it's also covering IBM i 6.1 and 6.1.1 with the patches; only IBM i versions 7.1 to 7.3 were patched in October.
The PTFs essentially disable 3DES across all IBM-controlled programs and utilities, including the SSL/TLS facilities in the IBM i Licensed Internal Code (LIC); the OpenSSL implementation in PASE; the Java JSSE-based IBMJSSE2 utility; and Domino, which contains an embedded SSL implementation (although it also uses the System SSL/TLS facility in some configurations).
The PTFs will activate newer and more secure AES ciphers in these IBM products. 'Not disabling the Triple DES (3DES) cipher or algorithm will expose yourself to the attack described above,' IBM writes in its security alert.
Why is 3DES being removed? Simply put, it's because 3DES is not considered highly secure anymore. The reasons have largely to do with the fact that the 3DES algorithm uses 64-bit block sizes, and those block sizes are no longer deemed sufficient by the security community to keep vigilant cybercriminals at bay. AES, by comparison, uses a 128-bit block size, which makes a big difference in preventing potentially sensitive data that could expose plaintext keys from leaking out.
'It is well-known in the cryptographic community that a short block size makes a block cipher vulnerable to birthday attacks, even if there are no cryptographic attacks against the block cipher itself,' write security researchers Karthikeyan Bhargavan and Gaëtan Leurent on the website sweet32.info, which is an excellent source for information on the SWEET32 vulnerability and how hackers can pull off brute-force 'birthday' style attacks that uses the laws of probability and big data to crack one-way hashing algorithms.
With the 3DES algorithm encrypting data across an HTTPS connection, the researchers determined that an attacker executing a SWEET32-based birthday attack could retrieve the plaintext keys (in the form of HTTP cookies) by capturing about 785GB of traffic between a Web browser and a server. That would require the HTTPS connection to be live for about two days, which may sound impractical (and is why the vuln garnered a relatively low security threat rating). But considering the financial motivation that hackers have and the increasingly sophisticated tools at their disposal, there's no reason to take a chance by using older, weaker cipher technology when newer and stronger ciphers like AES are readily available.
The good news is that 128-bit AES encryption is still considered practically unbreakable and is supported in popular network security protocols like OpenSSL, TLS, and SSH. AES (which is also available in 256-bit strength) should be considered the only safe encryption algorithm to use at this point. Many popular websites use it, and Web browsers support it. It's supported in the IBM i stack.
The bad news is that there's still a lot of 3DES out there. Because some Web browsers enable 3DES before AES by default, and because there are a lot of misconfigured servers out there, AES is still used in 1 to 2 percent of the world's Web traffic secured with the TLS protocol, according to Bhargavan and Leurent. (SSL, you will remember, is considered weak; TLS is its replacement.)
For IBM i shops that take security seriously, it's important to get on the right side of this. IBM is eliminating 3DES from its products. But the average IBM i shop runs a lot of non-IBM code, including FTP and Telnet utilities developed by third-party vendors. This is why it's critical for IBM i shops to check their software inventory and upgrade all of the vulnerable products.
According to IBM i security expert Patrick Townsend, this should be a priority item for IBM i shops. 'This one is important and you should take a look at it right away,' he writes on his Data Privacy Blog.
While Townsend Security uses the IBM i System SSL/TLS library in its products and is thus protected via IBM's remediation work, there are a handful of third-party software vendors that have their own implementations of OpenSSL, which requires them to fix the problem themselves.
Customers will need to make sure that 3DES is being removed from these special ports of OpenSSL, he says. 'You need to be talking to them right away,' Townsend writes in the blog post. 'Unfortunately I know of one or two that are no longer supporting the IBM i platform. So you may have some difficulty getting resolution on this issue.'
You can read IBM's security alert at www-01.ibm.com/support/docview.wss?uid=nas8N1021697.
RELATED STORIES
3DES is probably the most studied cryptographic algorithm ever. It offers the strength equivalent to a 112-bit block cipher. The best attacks published require massive amounts of storage and still take more than 2 108 operations. CAST is a well studied 128-bit algorithm. There is no known way of breaking it faster then brute force. The average rectum is roughly 12 centimeters (about 5 inches) long, but you're better off listening to your body than focusing on that number. Take fisting, for example. Triple DES encryption process It works by taking three 56-bit keys (K1, K2 and K3), and encrypting first with K1, decrypting next with K2 and encrypting a last time with K3. 3DES has two-key and three-key versions. Using the fastest computer in the world you will be able to process 2.932848e+24 possible combinations per year. 930.10^15. 60. 60. 24. 365 = 2.932848e+24 If you had this super computer running all day every day to crack one single encryption key of 128 bits. I would take roughly 68.5 years to go through all the possible combinations. Add just one more character ('abcdefgh') and that time increases to five hours. Nine-character passwords take five days to break, 10-character words take four months, and 11-character passwords take 10 years. Make it up to 12 characters, and you're looking at 200 years' worth of security – not bad for one little letter.
Think your password is secure enough?
How Long Does It Take To Crack 3des For Pc
You may want to think again. In 2014, nearly half of Americans had their personal info exposed by hackers – and that doesn't even count the many companies that experienced breaches.
And with more and more businesses storing their information in the cloud and using SaaS solutions like business intelligence and hr software platforms, keeping your information safe becomes even more important.
Selecting an obscure and complex password and changing it frequently can spell the difference between keeping your data secure and having your personal information stolen. We've gathered insights and advice to empower you to tighten up your online security – and keep hackers out of your personal business.
To get started, we set out to discover just how quickly a seasoned cracker could 'brute-force' various types of passwords (systematically check combinations until finding the correct one) based on factors such as length and character types. We also created an interactive feature that lets you estimate how long it would take someone to crack a password now compared with how long it took in the past. If you come up with an idea for a potential password, our tester can tell you just how secure it is. Just how many days, weeks, or years worth of security an extra letter or symbol make? How does password strength change over time? The answers just might surprise you.
How strong is a typical password now – and how strong was it in the 1980s? Enter a word (not your current password) and drag the slider to select a year to find out how long it would take for someone to crack the term if it were your password. It could take anywhere from infinite time to a millennium to mere fractions of a millisecond.
You can turn the 'word list' function on or off as you test passwords. This tool works by cycling through a word list containing common words and passwords and then evaluating other factors such as character types. If you enter a password not on the word list, the cracking time will not be affected. But if your password is on the word list, it greatly affects cracking time.
Note: The interactive tool is for educational purposes only. Although it does not collect or store your passwords, you should avoid using your current password.
How long should your password be?
When it comes to passwords, one thing is certain: Size matters. Adding a single character to a password boosts its security exponentially. In a so-called 'dictionary attack,' a password cracker will utilize a word list of common passwords to discern the right one. The list above shows the difference that adding characters can make when it comes to security.
For instance, if you have an extremely simple and common password that's seven characters long ('abcdefg'), a pro could crack it in a fraction of a millisecond. Add just one more character ('abcdefgh') and that time increases to five hours. Nine-character passwords take five days to break, 10-character words take four months, and 11-character passwords take 10 years. Make it up to 12 characters, and you're looking at 200 years' worth of security – not bad for one little letter.
alpha and numberic characters
Combining numbers and letters rather than sticking with one type of character dramatically enhances password security. A string of nine letters or numbers takes milliseconds to crack. Add a single letter, and your password may become cryptic enough to thwart password crackers for nearly four decades.
However, it's not as simple as swapping your 'e' for a '3' or adding a number at the end of a string of letters. Password attacking methods actually take advantage of those common habits. Your best bet is to simply make your password less predictable and more complicated.
asci, lowercase, and numeric characters
Combining several types of characters is an extremely effective way to make your password more cryptic. A simple, common word can be cracked in fractions of a millisecond. Inject a mix of lowercase and uppercase letters, numbers, and symbols (think @, %, and #), and your password can be secure for more than a decade.
password strength over time
Not every security issue comes down to password character types and length – time is also a major factor. Over the years, passwords weaken dramatically as technologies evolve and hackers become increasingly proficient. Castlevania the dracula x chronicles usa psp iso cso download. For example, a password that would take over three years to crack in 2000 takes just over a year to crack by 2004. Five years later, in 2009, the cracking time drops to four months. By 2016, the same password could be decoded in just over two months. This demonstrates the importance of changing passwords frequently.
How Long Does It Take To Crack 3des For Windows 10
what if you get hacked?
One morning, you open your email, and everything has gone haywire: Friends are chatting you to say they've received spam from your address. Your login history looks odd. You have a pile of bounce-back messages in your inbox and a bunch of strange messages in your sent box. You've been hacked – so what should you do?
First, recover your email account, and change your password (use our guidelines to formulate a strong one). Complete all the steps, such as changing security questions and setting up phone notifications. Because email is filled with personal information, you should also notify your bank, PayPal, online stores, and any other accounts to discern whether a breach has occurred. Be sure to change other passwords as well. Finally, notify your contacts in case emails sent from your account have compromised their information too. While not getting hacked at all is the best-case scenario, promptly taking these steps can make the best of a bad situation.
Protect yourself
As time goes on, it only becomes more likely that your password will be hacked – putting your most personal information at risk. By taking a few steps to enhance your password, you can exponentially minimize the risk of a breach. When it comes to passwords, size trumps all else – so choose one that's at least 16 characters. And be sure to choose a mix of character types (numbers, uppercase and lowercase letters, and symbols) to further enhance its security.
What else can you do? Steer clear of words found in the dictionary, pronouns, usernames, and other predefined terms, as well as commonly used passwords – the top two in 2015 were '123456' and 'password' (yes, you read that right). Also, never use the same password in different places (that forgotten account at a site you never use could lead to a bank account breach). Consider using a password generator in order to get a complex password with no discernible pattern to help thwart password crackers. Finally, if memorizing long strings of characters proves too taxing, consider adopting a password manager that stores all your passwords. No password is perfect, but taking these steps can go a long way toward security and peace of mind.
Methodology
Using processor data collected from Intel and John the Ripper benchmarks, we calculated keys per second (number of password keys attempted per second in a brute-force attack) of typical personal computers from 1982 to today.
The results from our interactive feature may differ from those of other online password-testing tools due to factors such as different equations, processors, and word lists.
Our data are based on the following equations:
Number of possible character combinations:
(Password Type)^(Password Length)
Password Type is the number of possible characters.
Effective Cores:
1/((1-Efficiency Constant)+(Efficiency Constant/Processor Cores)) The Efficiency Constant we used is 0.99, and we assume that 99% of the processor's operations can be dedicated to the password crack.
Processor GFLOPS:
How Long Does It Take To Crack 3des For Windows 7
Processor Frequency * Effective Cores
Keys Per Second:
How Long Does It Take To Crack 3des Free
GFLOPS/Encryption Constant (gathered and calculated from John the Ripper benchmarks).
Time in seconds:
Seconds = Combinations/KeysPerSecond
How Long Does It Take To Crack 3des Without
Sources
Fair Use
Feel free to share the images and interactive found on this page freely. When doing so, please attribute the authors by providing a link back to this page and Better Buys, so your readers can learn more about this project and the related research.
